The information provided in this site is for educational purposes regarding pentesting. The author of the site will not be held any responsibility for any misuse of the information from this site.
Introduction
This is the first part of my exploit development series. The first part will cover the basic things like Ideology, Mechanism behind exploits and a couple of things to keep in mind if we want to get to and execute our shellcode. This series will be long and will later cover how to find bugs, This series will also cover ROP (Return Oriented Programming)” and some other vulnerability and exploitation technique, This series will be starting with basics and then will initially move to advanced topics.This is the first part of my exploit development series. The first part will cover the basic things like Ideology, Mechanism behind exploits, and a couple of things to keep in mind if we want to get to and execute our shellcode. This series will be long and will later cover how to find bugs, This series will also cover ROP (Return Oriented Programming) and some other vulnerability and exploitation technique, This series will be starting with basics and then will initially move to advance topics.
Tools and other Plugins
x64dbg is an open-source binary debugger for the Windows operating system, used in reverse engineering executables, and analyzes malware There are many features of dbg debugger and a rich plugin system.
Immunity Debugger Immunity Debugger has python support which is suitable for available plugins plugin’s that will help us in our exploit development. You can download the Immunity Debugger from https://www.immunityinc.com/.
Cutter The cutter is a graphical user interface for radare2, It is a well-known reverse engineering tool, it is a cross-platform tool that supports Linux, Windows, and mac OS.
mona.py Mona is an outstanding tool that has tons of features that will help us to fasten the process and develop reliable exploit development. This can be added to our debugger. you can download the mona plugin from https://github.com/corelanprojects/mona/repository
Metasploit Framework When writing exploits to be used in the Metasploit Framework this allows us to generate our shell code which is further used in the exploit, Exploits include buffer overflow, code injection, and web application exploits.
Registers and imporant terms
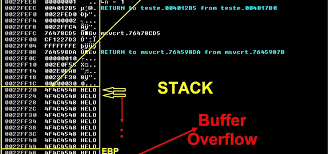
As this part covers basics only, starting with the exploits, when we write an exploit we look for an overflow in a program. Basically these vulnerabilities will be in form of Buffer Overflows (transaction overwrites executable code) or Stack Overflows (which is a Buffer Overflow that writes crossing the end of the stack). When an overflow exists there is a possibility two things might take place one if the buffer needs to overwrite EIP or one of the CPU registers needs to bounds the buffer. Below is a list of x86 CPU registers with their functions and any of the following register can store our buffer and shellcode. we start with a program to store an excessively long string, this string overwrites EIP and some portion of it is put away in a CPU register, we discover a pointer that focuses on the register that contains our buffer, we put that pointer in the right spot in our cushion so it overwrites EIP, when the program arrives at our pointer it executes the instruction and leaps to the register that contains our buffer lastly we place our shellcode in the piece of the buffer that is put away in the CPU register. Then we capture the execution stream and guide it toward a zone of memory that we control. On the off chance that we can do that we can need to remote machine execute any instruction.
Registers
1) EAX - Main register used in arithmetic calculations. Also known as an accumulator, as it holds results of arithmetic operations and function return values.
2) EBX - The Base Register. Pointer to data in the DS segment. Used to store the base address of the program.
3) ECX - The Counter register is often used to hold a value representing the number of times a process is to be repeated. Used for loop and string operations.
4) EDX - A general-purpose registers. Also used for I/O operations. Helps extend EAX to 64-bits.
5) ESI - Source Index register. Pointer to data in the segment pointed to by the DS register. Used as an offset address in the string and array operations. It holds the address from where to read data.
6) EDI - Destination Index register. Pointer to data (or destination) in the segment pointed to by the ES register. Used as an offset address in the string and array operations. It holds the implied write address of all string operations.
7) EBP - Base Pointer. Pointer to data on the stack (in the SS segment). It points to the bottom of the current stack frame. It is used to reference local variables.
8) ESP - Stack Pointer (in the SS segment). It points to the top of the current stack frame. It is used to reference local variables.
9) EIP - Instruction Pointer (holds the address of the next instruction to be executed)
